Did you know 24 percent of enterprise devices will never receive protection against critical vulnerabilities? Here’s how to keep your mobile data out of the hands of hackers.
Corporate data has moved beyond your four walls and now lives on employees’ mobile devices. This makes smartphones, tablets, and other devices a prime target for attacks.
Hackers are now launching Rowhammer attacks against Android phones.
After an Android user visits a malicious web page, the exploit installs code that causes memory cells to “flip” their ones and zeros. This alters the information stored in the device’s memory. This is “the first ever remote, smartphone-targeted implementation of the Rowhammer attack,” according to Wired.
The Elephant in the Room: Unsecured Android Devices
Attacks against Androids will continue to increase, as they are easy targets.
Many Android devices are released with operating systems that are already a year old.
On top of that, these devices are rarely – if ever – patched.
In fact, 71 percent of all Android users on the five major U.S. carriers are running security patches that are at least two months old, according to a Symantec study.
Meanwhile, Google revealed that half of the Android devices in use had not received a platform security update in the previous year.
The following graph from Symantec shows the frequency of Android patching. By the time devices are five months old, only three percent of them receive monthly patches.
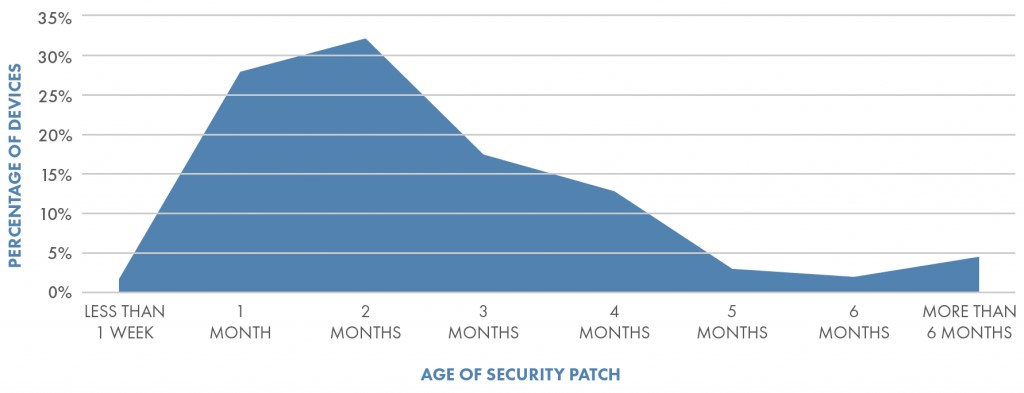
Source: Symantec Mobile Threat Intelligence Report
Unsecured mobile devices are a major threat to U.S. enterprises. In fact, the Federal Trade Commission addressed the issue. The FTC’s report states that many devices “remain without important security updates for long periods – either because no update is issued at all, because approving and deploying a patch is a lengthy process, or because users do not install available updates.” The report also states that while devices with robust support are available, they “can be hard to identify because manufacturers tend to make little information about support periods available before purchase.”
3 Ways to Protect Your Enterprise’s Mobile Devices
With so little protection out-of-the-box, enterprises must find other ways to keep their mobile devices secure.
Here are three steps that will help you protect your sensitive data:
-
Choose a platform that can be patched
This may not go over well in your company, but you should consider banning the use of Android devices since they are not secure enough for enterprise use.
Employees are often attached to their phones and many won’t like giving up their Androids. But you can’t allow unpatched and uncontrolled devices on your network. Create a company policy that states that employees can only use secure devices for work.
Apple patches their phones and has greater rigor in their application store, so the iPhone is a better choice. Symantec states, “Apple’s iOS devices typically have a rapid adoption of security updates because the software, hardware and distribution mechanism are all tightly integrated. This is not the case for Android, which supports multiple hardware platforms and components across multiple mobile carriers, each who must create their own variation of the security patch before distribution.”
However, employees may not need to be without their Google devices for long.
Google is investing in mobile security and now offers a Pixel phone that can be reliably patched. The future of Android may be Google’s Fuchsia OS.
-
Mandate patching
For secure organizations, patching your mobile devices isn’t optional as your employees now store sensitive data on them. You can improve your devices’ security by mandating that employees install patches.
From mobile device management platforms, you can force employees to patch their phones. For example, if they don’t patch their phones, they won’t be able to access their email accounts.
-
Keep an eye on your network
An intrusion detection system will help you identify compromised devices and alert you about potential threats, such as beaconing infections or phishing attacks. Beaconing infections – where a compromised asset signals to a known bad host – are becoming more common. You can also run a daily scan of your network to locate vulnerable devices.
Be sure to check your inventory on a regular basis to see if employees are adding rogue devices to your network. That way, you can proactively address a problem before a hacker breaks into your network via an employee’s mobile device. You can also monitor dangerous behavior, such as employees trying to install unauthorized apps on their phones.
The Future of Your Mobile Device Security
Although mobile device attacks are on the rise, there hasn’t been a major cell phone “WannaCry” event, yet. For this reason, many companies have been slow to protect their mobile devices and ensure that they are regularly patched.
However, it’s just a matter of time before an attack against a company’s mobile devices makes the headlines. You don’t want to be a trailblazer in this area.
Working with a managed service provider (MSP) can help you secure your mobile devices – keeping them patched and compliant. An MSP can take steps to protect your data, such as installing endpoint and malware protection on your company’s devices.
They can also monitor your devices 24/7 for suspicious activity.
Next Steps
To learn more about how to secure your enterprise’s mobile devices, we suggest you read:
- What you should know about endpoint security
- Why and how to block security breaches at the endpoint
- 10 questions to determine if your IDPS is set up properly
You can also contact us today to discover how we can help you protect your company’s mobile devices.

