PLATFORMS
AWS Security is infused with Syntax Managed Services
Syntax delivers its managed services with a comprehensive, integrated and best-practice driven approach that is aimed at ensuring the integrity of hosted ERP applications and the data they store and process.
The Syntax security goal is pursued by infusing security practices and protocols throughout its design, processes, and systems & standards, such as Security Operations Center SOC 1 and SOC 2.
This complements our wide range of AWS offerings as Premier Consulting Partner including our SAP, Oracle, and Migration competencies, MSP designation as well as our validated qualification on the AWS Well-Architected program.

The Fundamental AWS Managed Security Services (MSS) Implemented by Syntax
Syntax MSS includes 24×7 fully managed security services that have been designed following the AWS security pillars that will ensure protection, monitoring, and response to security events of critical ERP managed systems hosted on AWS cloud.
An effective and complete security framework where each component is designed to take advantage of AWS security services combined with Syntax ERP and cloud expertise.

1. AWS Infrastructure Vulnerability Scanning

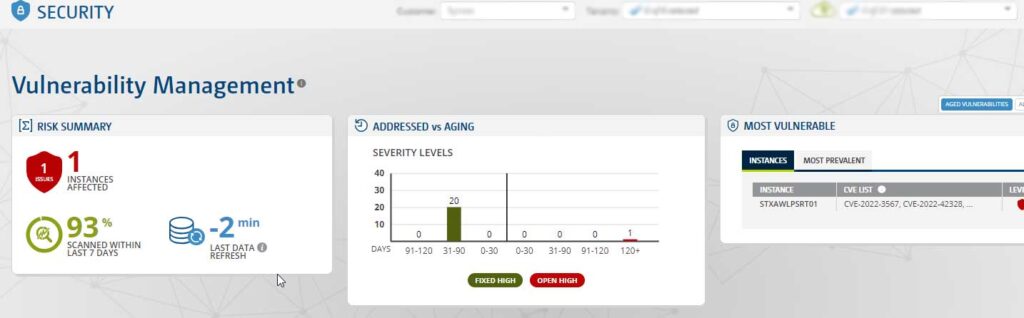
Managed Vulnerability Management as a service, meaning managed assessment and remediation of identified vulnerabilities.

Realtime Discovery with Dynamic Alerts for newly discovered vulnerabilities that can be weaponized (threats).
2. AWS Resource Inventory Visibility
Syntax Customer Experience Hub (CxHub) provides full visibility to the customer’s environment by AWS instance, as well as Vulnerability and EDR Management.
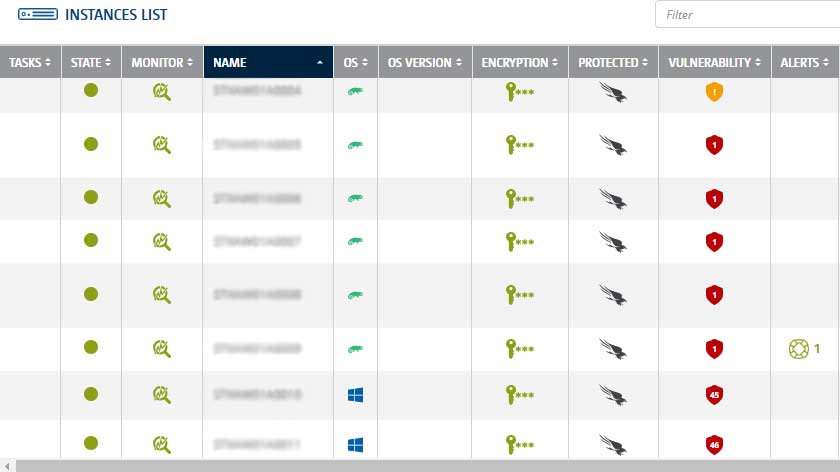
3. AWS Security Best Practices Monitoring
Syntax’s Security Services encompass AWS Security best practices with our internal monitoring system. Syntax also provides AI/ML and proprietary tooling and automation to address security management:
Enable traceability
Monitor, alert, and audit actions and changes to the environment in real time. Integrate logs and metrics with systems to automatically respond and act.
Automate security best practices
Automated software-based security mechanisms improve the ability to securely scale more rapidly and cost effectively.
4. AWS Compliance Monitoring
Security and Compliance is a shared responsibility between AWS, Syntax, and the customer. Using internal solutions as well as AWS services such as AWS Artifact, AWS GuardDuty, AWS Shield and AWS CloudTrail, Syntax ensures your compliance and regulatory requirements are met, covering over the 140 standards and compliance certifications. AWS Compliance Center, Syntax CxHub and AWS Organizations help centrally govern and manage billing; control access (IAM), compliance, and security.
Additionally, Syntax CxHub provides visualization of compliance status across the customer’s AWS tenant, based on the AWS Well-Architected Framework.
5. Cloud Security Posture Management
CSPM is a set of tools and practices that provide continuous monitoring, assessment, and remediation of security risks and misconfigurations across cloud environments.
- Discovery and visibility into cloud assets, configurations, and changes across multi-cloud environments.
- Continuous monitoring and assessment of cloud security posture against defined policies and standards.
- AI enhanced remediation of misconfigurations and policy violations.
- Real-time threat detection and incident response for unauthorized activities or access.
- Integration with Security Operations workflows (SecOps) to embed security throughout the cloud landscape.
- Helps prevent data breaches and minimizes the impact of cloud misconfigurations.
CSPM is a crucial component of cloud security that helps organizations maintain a strong security posture, ensure compliance, and minimize the risks associated with cloud adoption and misconfigurations.
6. Monitor, Triage Security Events
Syntax Managed Security customers are protected using a variety of AWS tools and Syntax integrated systems including:
AWS CloudWatch
Monitoring the resources and applications supporting ERP customers.
AWS CloudTrail
Monitoring the applications and the infrastructure performance in the AWS environment, Syntax funnels all events from these systems into our internal systems to provide Machine Learning Driven integration into our SIEM systems. We then triage those events to remove the non-essential items and create SLA driven tickets to resolve high risk or actionable events for customers.
7. 24/7 Incident Alerting and Response: Syntax Global Security Operations Center (SOC)
The Syntax SOC is staffed around the clock, 24 hours a day, 7 days a week, 365 days a year by our in-house team of experienced cybersecurity professionals. Our customers find this critical because acquiring and retaining talented security professionals in today’s competitive environment is challenging. By relying on the Syntax SOC, customers can transfer the heavy lifting of security analysis for their environment to Syntax and benefit from our team’s experience working hundreds of incidents per week.
8. Distributed Denial of Service (DDoS) Mitigation
Syntax uses AWS Shield as a Managed Distributed Denial of protection service (DDoS) that safeguards applications running on AWS against the more common, most frequently observed DDoS attacks. The service is enabled by default for all AWS customers. Additionally, with AWS Web Applications Firewall, Syntax customers can mitigate DDoS attacks. Events and reporting on DDoS are sent to the Syntax SOC for monitoring and triage.
9 & 10. Managed Intrusion Detection/Prevention System & Managed detection and response for AWS based endpoints
Syntax Endpoint Protection, which encompasses our SOC Services to manage, report and act on Security Events is crucial to our AWS hosted customers on a managed basis.
Syntax Endpoint Protection is designed to monitor customers’ AWS-hosted endpoint devices for suspicious activity and provide real-time visibility into the state of the devices and their security posture. An additional function is to provide detailed information about the security events and incidents that occur on the devices, including information about the processes, files, and network connections that are associated with the events.
Syntax managed AWS endpoint solutions are becoming increasingly important as organizations adopt a Zero Trust model and attempt to secure access to resources in mobile and distributed environments. The ability to detect and respond to security threats on endpoint devices is essential for maintaining a strong security posture and protecting against cyber threats.
11. Managed Web Application Firewall (WAF)
AWS WAF helps protect customers web applications or APIs against common web exploits that may affect availability, compromise security, or consume excessive resources. AWS WAF gives control over how traffic reaches applications by enabling the creation of security rules that block common attack patterns, such as SQL injection or cross-site scripting, and rules that filter out specific traffic patterns defined.
Syntax uses WAF for customers that want to expose their applications on the internet. More specifically, customers that require restrictions for Geo-IPs to block certain countries. WAF provides advanced web application protection and helps remediate compliance concerns.